[New Updated Questions] Latest Cisco CCNA 210-255 Dumps SECOPS Practice Exam Questions With New Discount 210-255 Dumps Youtube Study Guide
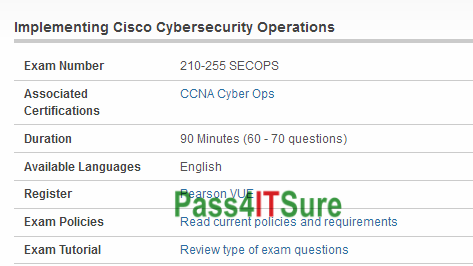
What are some good blogs to learn Cisco 210-255 dumps and clear? The Implementing Cisco Cybersecurity Operations (210-255 SECOPS) exam is a 90 Minutes (60 – 70 questions) assessment in pass4itsure that is associated with the CCNA Cyber Ops certification. Latest Cisco CCNA 210-255 dumps SECOPS practice exam questions with new discount 210-255 dumps Youtube study guide. “Implementing Cisco Cybersecurity Operations” is the exam name of Pass4itsure Cisco 210-255 dumps test which designed to help candidates prepare for and pass the Cisco 210-255 exam. Most of the students feel hesitate to learn individually about https://www.pass4itsure.com/210-255.html dumps questions braindumps as they think with valid 210–255 dumps. For those individual learners we have valid 210–255 sample questions for Implementing Cisco Cybersecurity Operations preparation.
[New Updated Cisco 210-255 dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWOXlNazlKRi1GcFU
[New Updated Cisco 010-151 dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWSno1cV9ERFZGZXc
Share Some Cisco Specialist 210-255 Dumps Exam Questions and Answers Below:
QUESTION NO: 117
Which of the following phases of the DITSCAP C&A process is used to define the C&A level of effort, to identify the main C&A roles and responsibilities, and to create an agreement on the method for implementing the security requirements?
A. Phase 1
B. Phase 4
C. Phase 2
D. Phase 3
210-255 exam Answer: A
Explanation: The Phase 1 of the DITSCAP C&A process is known as Definition Phase. The goal of this phase is to define the C&A level of effort, identify the main C&A roles and responsibilities, and create an agreement on the method for implementing the security requirements. Answer: C is incorrect.
The Phase 2 of the DITSCAP C&A process is known as Verification. Answer: D is incorrect.
The Phase 3 of the DITSCAP C&A process is known as Validation. Answer: B is incorrect.
The Phase 4 of the DITSCAP C&A process is known as Post Accreditation.
QUESTION NO: 118
Which of the following types of obfuscation transformation increases the difficulty for a de obfuscation tool so that it cannot extract the true application from the obfuscated version?
A. Preventive transformation
B. Data obfuscation
C. Control obfuscation
D. Layout obfuscation
Answer: A
Explanation: Preventive transformation increases the difficulty for a de-obfuscation tool so that it cannot extract the true application from the obfuscated version.
QUESTION NO: 119
Which of the following techniques is used when a system performs the penetration testing with the objective of accessing unauthorized information residing inside a computer?
A. Biometrician
B. Van Eck Phreaking
C. Port scanning
D. Phreaking
210-255 dumps Answer: C
Explanation: Port scanning identifies open doors to a computer. Hackers and crackers use this technique to obtain unauthorized information. Port scanning is the first basic step to get the details of open ports on the target system. Port scanning is used to find a hackable server with a hole or vulnerability. A port is a medium of communication between two computers. Every service on a host is identified by a unique 16-bit number called a port. A port scanner is a piece of software designed to search a network host for open ports. This is often used by administrators to check the security of their networks and by hackers to identify running services on a host with the view to compromising it. Port scanning is used to find the open ports, so that it is possible to search exploits related to that service and
application. Answer: D is incorrect. Phreaking is a process used to crack the phone system. The main aim of phreaking is to avoid paying for long- distance calls. As telephone networks have become computerized, phreaking has become closely linked with computer hacking. This is sometimes called the H/P culture (with H standing for Hacking and P standing for Phreaking).
Answer: A is incorrect. It is defined as a system using a physical attribute for authenticating. Only authorized users are provided access to network or application.
Answer: B is incorrect. It is described as a form of eavesdropping in which special equipments are used to pick up the telecommunication signals or data within a computer device.
QUESTION NO: 120
Which of the following types of attacks is targeting a Web server with multiple compromised computers that are simultaneously sending hundreds of FIN packets with spoofed IP source IP addresses?
A. DDoS attack
B. Evasion attack C.
Insertion attack D.
Dictionary attack
Answer: A
Explanation: A distributed denial of service (DDoS) attack targets a Web server with multiple compromised computers that are simultaneously sending hundreds of FIN packets with spoofed IP source IP addresses. DDoS attack occurs when multiple compromised systems flood the bandwidth or resources of a targeted system, usually one or more Web servers. These systems are compromised by attackers using a variety of methods. It is an attempt to make a computer resource unavailable to its intended users. This type of attack can cause the following to occur: Saturate network resources. Disrupt connections between two computers, thereby preventing communications between services. Disrupt services on a specific computer.
Answer: D is incorrect. Dictionary attack is a type of password guessing attack. This type of attack uses a dictionary of common words to find out the password of a user. It can also use common words in either upper or lower case to find a password. There are many programs available on the Internet to automate and execute dictionary attacks.
Answer: C is incorrect. In an insertion attack, an IDS accepts a packet and assumes that the host computer will also accept it. But in reality, when a host system rejects the packet, the IDS accepts the attacking string that will exploit vulnerabilities in the IDS. Such attacks can badly infect IDS signatures and IDS signature analysis.
Answer: B is incorrect. An evasion attack is one in which an IDS rejects a malicious packet but the host computer accepts it. Since an IDS has rejected it, it does not check the contents of the packet. Hence, using this technique, an attacker can exploit the host computer. In many cases, it is quite simple for an attacker to send such data packets that can easily perform evasion attacks on an IDSs.
QUESTION NO: 121
Which of the following programming languages are compiled into machine code and directly executed by the CPU of a computer system? Each correct answer represents a complete solution. Choose two.
A. C
B. Microosft.NET
C. Java EE
D. C++
210-255 pdf Answer: A,D
Explanation: C and C++ programming languages are unmanaged code. Unmanaged code is compiled into machine code and directly executed by the CPU of a computer system. Answer: C and B are incorrect. Java EE and Microsoft.Net are compiled into an intermediate code format.
QUESTION NO: 122
Which of the following is a standard that sets basic requirements for assessing the effectiveness of computer security controls built into a computer system?
A. FITSAF
B. FIPS
C. TCSEC
D. SSAA
Answer: C
Explanation: Trusted Computer System Evaluation Criteria (TCSEC) is a United States Government Department of Defense (DoD) standard that sets basic requirements for assessing the effectiveness of computer security controls built into a computer system. TCSEC was used to evaluate, classify, and select computer systems being considered for the processing, storage, and retrieval of sensitive or classified information. It was replaced with the development of the Common Criteria international standard originally published in 2005. The TCSEC, frequently referred to as the Orange Book, is the centerpiece of the DoD Rainbow Series publications.
Answer: D is incorrect. System Security Authorization Agreement (SSAA) is an information security document used in the United States Department of Defense (DoD) to describe and accredit networks and systems. The SSAA is part of the Department of Defense Information Technology Security Certification and Accreditation Process, or DITSCAP (superseded by DIACAP). The DoD instruction (issues in December 1997, that describes DITSCAP and provides an outline for the SSAA document is DODI 5200.40. The DITSCAP application manual (DoD 8510.1- M), published in July 2000, provides additional details. Answer: A is incorrect. FITSAF stands for Federal Information Technology Security Assessment Framework. It is a methodology for assessing the security of information systems. It provides an approach for federal agencies. It determines how federal agencies are meeting existing policy and establish goals. The main advantage of FITSAF is that it addresses the requirements of Office of Management and Budget (OMB). It also addresses the guidelines provided by the National Institute of Standards and Technology (NIsT).
Answer: B is incorrect. The Federal Information Processing Standards (FIPS) are publicly announced standards developed by the United States federal government for use by all non-military government agencies and by government contractors. Many FIPS standards are modified versions of standards used in the wider community (ANSI, IEEE, ISO, etc.). Some FIPS standards were originally developed by the U.S. government. For instance, standards for encoding data (e.g., country codes), but more significantly some encryption standards, such as the Data Encryption Standard (FIPS 46-3) and the Advanced Encryption Standard (FIPS 197). In 1994, NOAA (Noaa) began broadcasting coded signals called FIPS (Federal Information Processing System) codes along with their standard weather broadcasts from local stations. These codes identify the type of emergency and the specific geographic area (such as a county) affected by the emergency.
QUESTION NO: 123
Which of the following elements of BCP process includes the areas of plan implementation, plan testing, and ongoing plan maintenance, and also involves defining and documenting the continuity strategy?
A. Business continuity plan development
B. Business impact assessment
C. Scope and plan initiation
D. Plan approval and implementation
210-255 vce Answer: A
Explanation: The business continuity plan development refers to the utilization of the information collected in the Business Impact Analysis (BIA) for the creation of the recovery strategy plan to support the critical business functions. The information gathered from the BIA is mapped out to make a strategy for creating a continuity plan. The business continuity plan development process includes the areas of plan implementation, plan testing, and ongoing plan maintenance. This phase also consists of defining and documenting the continuity strategy. Answer: C is incorrect. The scope and plan initiation process in BCP symbolizes the beginning of the BCP process. It emphasizes on creating the scope and the additional elements required to define the parameters of the plan. The scope and plan initiation phase embodies a check of the company’s operations and support services. The scope activities include creating a detailed account of the work
required, listing the resources to be used, and defining the management practices to be employed.
Answer: B is incorrect. The business impact assessment is a method used to facilitate business units to understand the impact of a disruptive event. This phase includes the execution of a vulnerability assessment. This process makes out the mission-critical areas and business processes that are important for the survival of business. It is similar to the risk assessment process. The function of a business impact assessment process is to create a document, which is used to help and understand what impact a disruptive event would have on the business.
Answer: D is incorrect. The plan approval and implementation process involves creating enterprise-wide awareness of the plan, getting the final senior management signoff, and implementing a maintenance procedure for updating the plan as required.
QUESTION NO: 124
Which of the following refers to a process that is used for implementing information security?
A. Classic information security model
B. Five Pillars model
C. Certification and Accreditation (C&A)
D. Information Assurance (IA)
Answer: C
Explanation: Certification and Accreditation (C&A or CnA) is a process for implementing information security. It is a systematic procedure for evaluating, describing, testing, and authorizing systems prior to or after a system is in operation. The C&A process is used extensively
in the U.S. Federal Government. Some C&A processes include FISMA, NIACAP, DIACAP, and DCID 6/3. Certification is a comprehensive assessment of the management, operational, and technical security controls in an information system, made in support of security accreditation, to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system. Accreditation is the official management decision given by a senior agency official to authorize operation of an information system and to explicitly accept the risk to agency operations (including
mission, functions, image, or reputation), agency assets, or individuals, based on the implementation of an agreed-upon set of security controls. Answer: D is incorrect. Information Assurance (IA) is the practice of managing risks related to the use, processing, storage, and
transmission of information or data and the systems and processes used for those purposes. While focused dominantly on information in digital form, the full range of IA encompasses not only digital but also analog or physical form. Information assurance as a field has grown from the practice of information security, which in turn grew out of practices and procedures of computer security.
Answer: A is incorrect. The classic information security model is used in the practice of Information Assurance (IA) to define assurance requirements. The classic information security model, also called the CIA Triad, addresses three attributes of information and information systems, confidentiality, integrity, and availability. This C-I-A model is extremely useful for teaching introductory and basic concepts of information security and assurance; the initials are an easy mnemonic to remember, and when properly understood, can prompt systems designers and users to address the most pressing aspects of assurance. Answer: B is incorrect. The Five Pillars model is used in the practice of Information Assurance (IA) to define assurance requirements. It was promulgated by the U.S. Department of Defense (DoD) in a variety of publications, beginning with the National Information Assurance Glossary, Committee on National Security Systems Instruction CNSSI-4009. Here is the definition from that publication: “Measures that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation. These measures include providing for restoration of information systems by incorporating protection, detection, and reaction capabilities.” The Five Pillars model is sometimes criticized because authentication and non-repudiation are not attributes of information or systems; rather, they are procedures or methods useful to assure the integrity and authenticity of information, and to protect the confidentiality of the same.
You will be excited to know that you can get SECOPS 210–255 dumps without joining any IT institute. “Implementing Cisco Cybersecurity Operations”, also known as 210-255 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. But you will find CCNA Cyber Ops 210–255 questions and answers in no time in our https://www.pass4itsure.com/210-255.html dumps training material. Pass4itsure Cisco 210-255 dumps exam questions answers are updated (80 Q&As) are verified by experts. The associated certifications of 210-255 dumps is CCNA Cyber Ops.