200-301 Exam: The Importance Of 200-301 CCNA Dumps

When you want to enter the Cisco CCNA Certification, you must pass the 200-301 CCNA exam. In this case, getting 200-301 CCNA dumps is the beginning of your preparation for the exam.
Pass4itSure provides you with the latest updated 200-301 CCNA dumps real exam questions and answers to perfectly prepare for the exam and get excellent results on the real exam.
Get it here: https://www.pass4itsure.com/200-301.html
Why is a 200-301 CCNA dumps important?
The 200-301 CCNA dumps have several benefits that can be divided into the following two points.
The benefit of getting the 200-301 CCNA exam questions first is better preparation and understanding of the content and format of the exam, which improves your chances of passing the exam.
In addition, by practicing real exam questions with 200-301 CCNA dumps, you can better understand how well you have mastered the knowledge you need for the exam and the areas that need to be further strengthened.
What exactly should I do to pass the 200-301 exam?
To pass the 200-301 exam, you can try these three steps:
- Familiarize yourself with the exam content
- Learn related technologies
- Download the latest 200-301 dumps (Pass4itSure 200-301 dumps is good)
- Practice practice
In short, through systematic study and practice, coupled with adequate preparation for the exam, you may pass the 200-301 exam and obtain CCNA certification.
So, where can I get free 200-301 exam questions to practice?
Pmtrainingprep.com is ready for you.
200-301 CCNA dumps 2023 latest exam practice questions sharing
Question 1:
Which is the reason to implement IPv4 private addressing?
A. Comply with PCI regulations.
B. Reduce the size of the forwarding table on network routers.
C. Reduce the risk of a network security breach.
D. Comply with local law.
Correct Answer: C
Question 2:
How does STP prevent forwarding loops at OSI Layer 2?
A. TTL
B. MAC address forwarding
C. Collision avoidance
D. Port blocking
Correct Answer: D
Question 3:
Refer to the exhibit.
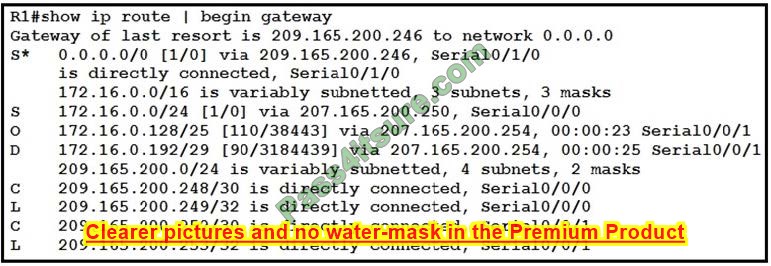
With which metric was the route to host 172.16.0.202 learned?
A. 0
B. 110
C. 38443
D. 3184439
Correct Answer: C
Both the line “O 172.16.0.128/25” and “S 172.16.0.0/24” cover the host 172.16.0.202 but with the “longest (prefix) match” rule the router will choose the first route.
Question 4:
Refer to the exhibit.
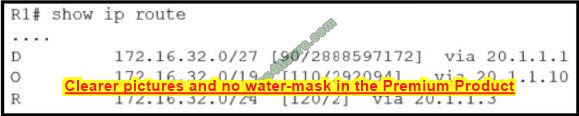
An engineer executed the script and added commands that were not necessary for SSH and now must remove the commands.
A. metric
B. cost
C. longest prefix
D. administrative distance
Correct Answer: D
Question 5:
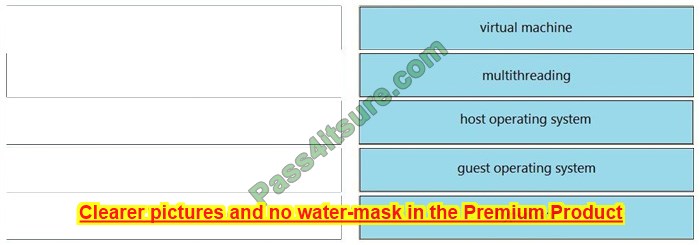
DRAG DROP
Drag and drop the virtualization concepts from the left onto the matching statements on the right.
Select and Place:
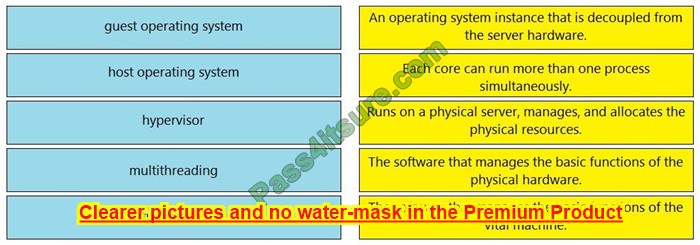
Correct Answer:
Question 6:
Which two network actions occur within the data plane? (Choose two.)
A. Add or remove an 802.1Q trunking header.
B. Make a configuration change from an incoming NETCONF RPC.
C. Run routing protocols.
D. Match the destination MAC address to the MAC address table.
E. Reply to an incoming ICMP echo request.
Correct Answer: AD
Actions DATA PLANE:
?De-encapsulating and re-encapsulating a packet in a data-link frame (routers, Layer 3 switches)
?Adding or removing an 802.1Q trunking header (routers and switches)
?Matching an Ethernet frame\’s destination Media Access Control (MAC) address to the MAC address table (Layer 2 switches)
?Matching an IP packet\’s destination IP address to the IP routing table (routers, Layer 3 switches)
?Encrypting the data and adding a new IP header (for virtual private network [VPN] processing)
?Changing the source or destination IP address (for Network Address Translation [NAT] processing)
?Discarding a message due to a filter (access control lists [ACLs], port security
Question 7:
Which three statements are typical characteristics of VLAN arrangements? (Choose three.)
A. A new switch has no VLANs configured.
B. Connectivity between VLANs requires a Layer 3 device.
C. VLANs typically decrease the number of collision domains.
D. Each VLAN uses a separate address space.
E. A switch maintains a separate bridging table for each VLAN.
F. VLANs cannot span multiple switches.
Correct Answer: BDE
Question 8:
Refer to the exhibit. When running EIGRP, what is required for RouterA to exchange routing updates with RouterC?

A. AS numbers must be changed to match on all the routers
B. Loopback interfaces must be configured so a DR is elected
C. The no auto-summary command is needed on Router A and Router C
D. Router B needs to have two network statements, one for each connected network
Correct Answer: A
This question is to examine the understanding of the interaction between EIGRP routers. The following information must be matched so as to create a neighborhood. EIGRP routers to establish must match the following information:
- AS Number;
2. K value.
Question 9:
What is the role of disaggregation in controller-based networking?
A. It divides the control-plane and data-plane functions.
B. It summarizes the routes between the core and distribution layers of the network topology.
C. It enables a network topology to quickly adjust from a ring network to a star network
D. It streamlines traffic handling by assigning individual devices to perform either Layer 2 or Layer 3 functions.
Correct Answer: A
Question 10:
Refer to the exhibit.
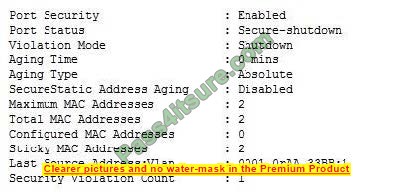
Which two statements about the interface that generated the output are true? (Choose two.)
A. Two secure MAC addresses are manually configured on the interface.
B. A Syslog message is generated when the maximum number of secure MAC addresses is on the interface.
C. The interface is error-disabled.
D. The interface dynamic ally learned two secure MAC addresses.
E. An SNMP trap is generated when the maximum number of secure MAC addresses is reached on the interface.
Correct Answer: CD
Question 11:
What are two characteristics of a public cloud Implementation? (Choose two.)
A. It is owned and maintained by one party, but it is shared among multiple organizations.
B. It enables an organization to fully customize how It deploys network resources.
C. It provides services that are accessed over the Internet.
D. It Is a data center on the public Internet that maintains cloud services for only one company.
E. It supports network resources from a centralized third-party provider and privately-owned virtual resources
Correct Answer: CE
Question 12:
Refer to the exhibit. Users on existing VLAN 100 can reach sites on the Internet. Which action must the administrator take to establish connectivity to the Internet for users in VLAN 200?
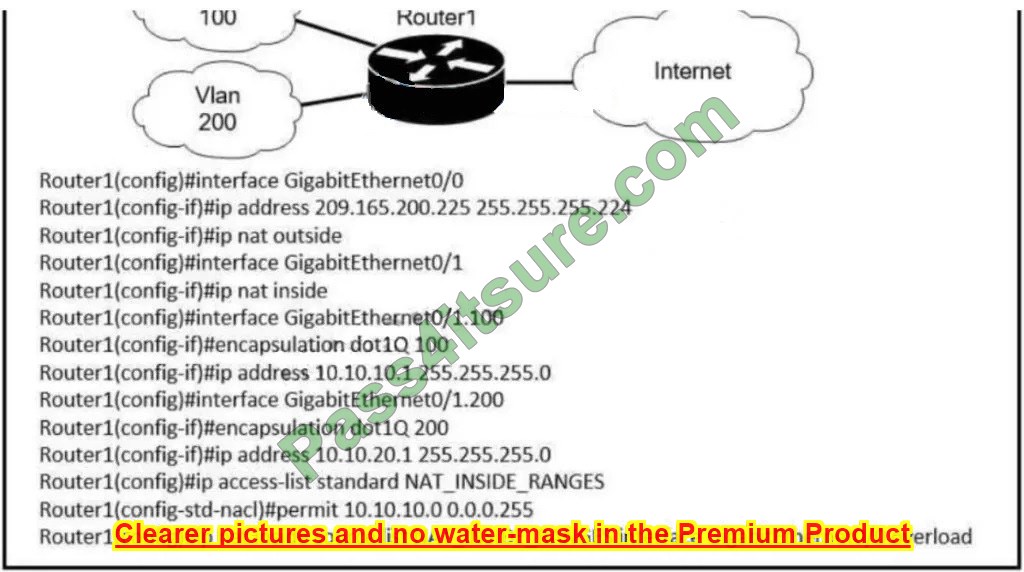
A. Define a NAT pool on the router.
B. Configure static NAT translations for VLAN 200.
C. Configure the ip nat outside command on another interface for VLAN 200.
D. Update the NAT_INSIDE_RANGES ACL
Correct Answer: D
Question 13:
Refer to the exhibit. Which two statements are true about the loopback address that is configured on RouterB? (Choose two.)
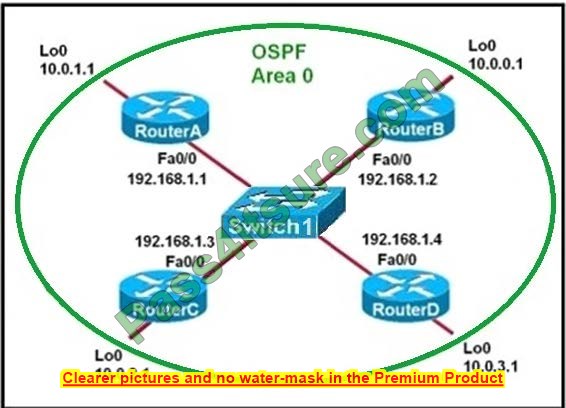
A. It ensures that data will be forwarded by RouterB.
B. It provides stability for the OSPF process on RouterB.
C. It specifies that the router ID for RouterB should be 10.0.0.1.
D. It decreases the metric for routes that are advertised from RouterB.
E. It indicates that RouterB should be elected the DR for the LAN.
Correct Answer: BC
A loopback interface never comes down even if the link is broken so it provides stability for the OSPF process (for example we use that loopback interface as the router-id) – The router-ID is chosen in the order below:
+ The highest IP address assigned to a loopback (logical) interface.+ If a loopback interface is not defined, the highest IP address of all active routers \’s physical interfaces will be chosen. -> The loopback interface will be chosen as the router ID of RouterB?
Question 14:
Refer to the exhibit.
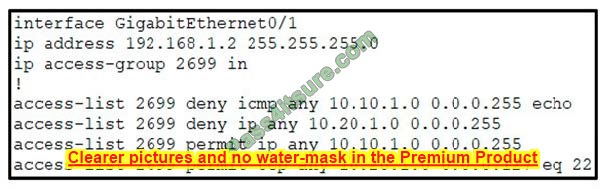
A network administrator must permit SSH access to remotely manage routers in a network. The operations team resides on the 10.20.1.0/25 network. Which command will accomplish this task?
A. access-list 2699 permit udp 10.20.1.0 0.0.0.255
B. no access-list 2699 deny tcp any 10.20.1.0 0.0.0.127 eq 22
C. access-list 2699 permits tcp any 10.20.1.0 0.0.0.255 eq 22
D. no access-list 2699 deny ip any 10.20.1.0 0.0.0.255
Correct Answer: D
Already a statement is there in the last to allow SSH Traffic for network 10.20.1.0 0.0.0.127, but the Second
statement says to deny ip any 10.20.1.0 0.0.0.255, so how it will work once it is denied? So the right answer is remove the — no access-list 2699 deny ip any 10.20.1.0 0.0.0.255.
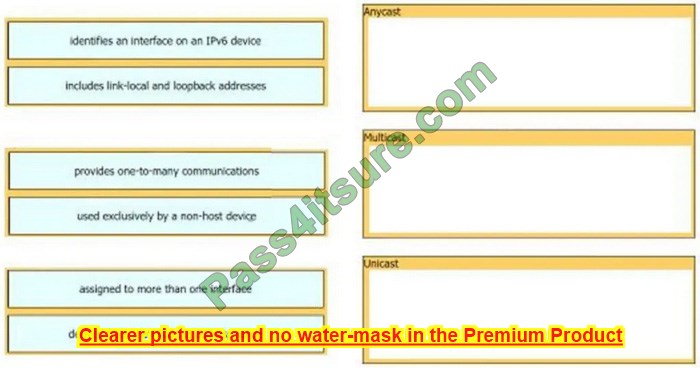
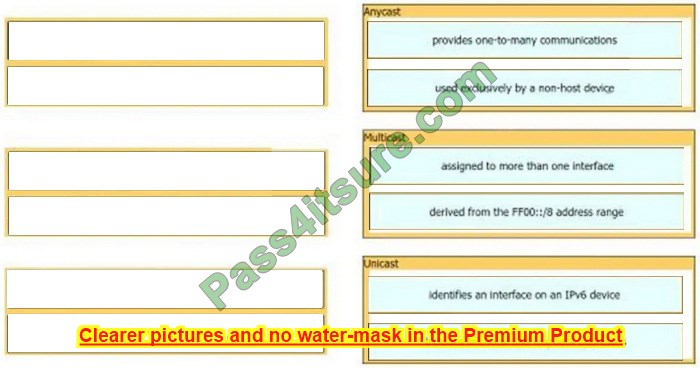
Question 15:
DRAG DROP
Drag and drop the IPv6 address details from the left onto the corresponding types on the right.
Select and Place:
Correct Answer:
For more questions, you need to download the Pass4itSure 200-301 CCNA dumps https://www.pass4itsure.com/200-301.html