Maximize exam scores with the new NS0-194 dumps.
Download the new NS0-194 Dumps 2024 (Pass4itSure) – Practice the real NS0-194 Dumps new practice questions 60+ https://www.pass4itsure.com/ns0-194.html PDF or VCE mode to prepare for the NetApp Certified Support Engineer exam.
As technology continues to advance at a rapid pace, it is becoming increasingly important for IT professionals to stay updated with the latest skills and knowledge. One way to demonstrate your expertise in the field is by obtaining relevant certifications. The NS0-194 certification exam is designed to validate your proficiency in NetApp Certified Support Engineer (NCSE) technology.
In this article, we will explore how you can maximize your exam performance by utilizing the new NS0-194 dumps.
Let’s start with the free NS0-194 practice questions that interest you the most.
2023 vs 2024
Let’s start with two sets of NS0-194 exam questions from different periods, so that you can learn and learn, and experience the latest meaning in the process of learning.
The following two sets of exercises are titled 2023 (December) and 2024 (as of now).
Share Free New NS0-194 Dumps NS0-194 Practice Questions(2023.12)
From: Pass4itSure
Number of issues: 15/60
More NetApp Certification Exams…
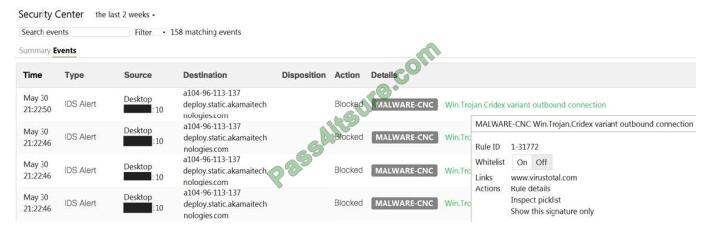
Question 1:
A customer has reported an unexplained reboot of an ONTAP node that did not generate a panic string or a core file.
In this scenario, which two sets of logs do you collect to further diagnose the issue? (Choose two.)
A. system core
B. sp status
C. events all
D. sp status -d
Correct Answer: AC
Question 2:
How many data-serving SVMs are supported with Cloud Volumes ONTAP that is running ONTAP 9.5?
A. 128
B. 1024
C. 1
D. 10
Correct Answer: C
Reference: https://docs.netapp.com/us-en/cloud-volumes-ontap/reference_limitations_95.html
Question 3:
A customer ordered a FAS2720 cluster with 8 TB SATA drives. The customer wants to use the Advanced Drive Partitioning (ADP) feature to avoid consuming the high-capacity drives for the root aggregate. Before you use the cluster setup, you issue the aggr status command and notice that ADP is not being used.
In this scenario, what would you use to implement ADP?
A. loader prompt
B. special boot menu
C. node shell
D. SP prompt
Correct Answer: A
Question 4:
You observe cyclic redundancy check (CRC) errors on a network port from a node in the cluster.
Which two components would you consider reseating or replacing before you perform actions on the physical port where the errors are reported from the node? (Choose two.)
A. SFP
B. cluster interconnect switch
C. up-stream switch
D. cable
Correct Answer: CD
Question 5:
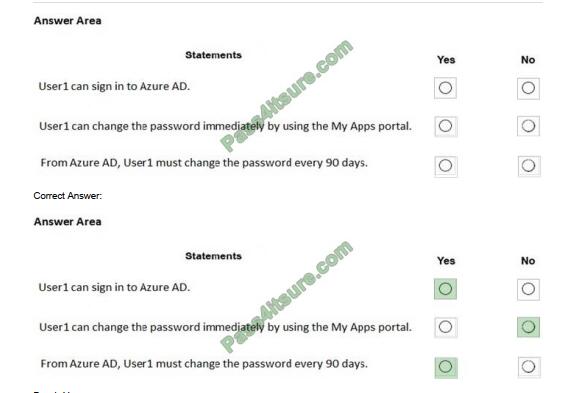
Your Windows clients were able to access your CIFS SVM yesterday. Today they are no longer able to access the CIFS SVM on your NetApp cluster. Your IT security team just pushed out a new group policy to enhance security.
In this scenario, which statement is true?
A. Your CIFS SVM is not using DNS.
B. Your CIFS SVM is configured to use SMBv1 and SMBv2.
C. Your CIFS SVM is configured for NFSv3 access.
D. Your CIFS SVM is configured for the wrong domain.
Correct Answer: A
Question 6:
When you replace a motherboard, which step will completely test the newly installed component?
A. From ONTAP, execute sldiag.
B. From the LOADER prompt, type boot_ontap maint, then execute sliding.
C. From the LOADER prompt, type boot_diags, then execute sldiag.
D. From the LOADER prompt, execute sliding.
Correct Answer: B
Reference: https://library.netapp.com/ecm/ecm_download_file/ECMP1199896 (36)
Question 7:
What is the minimum number of compute nodes required to run the NetApp Deployment Engine for NetApp HCI?
A. 2
B. 1
C. 3
D. 4
Correct Answer: A
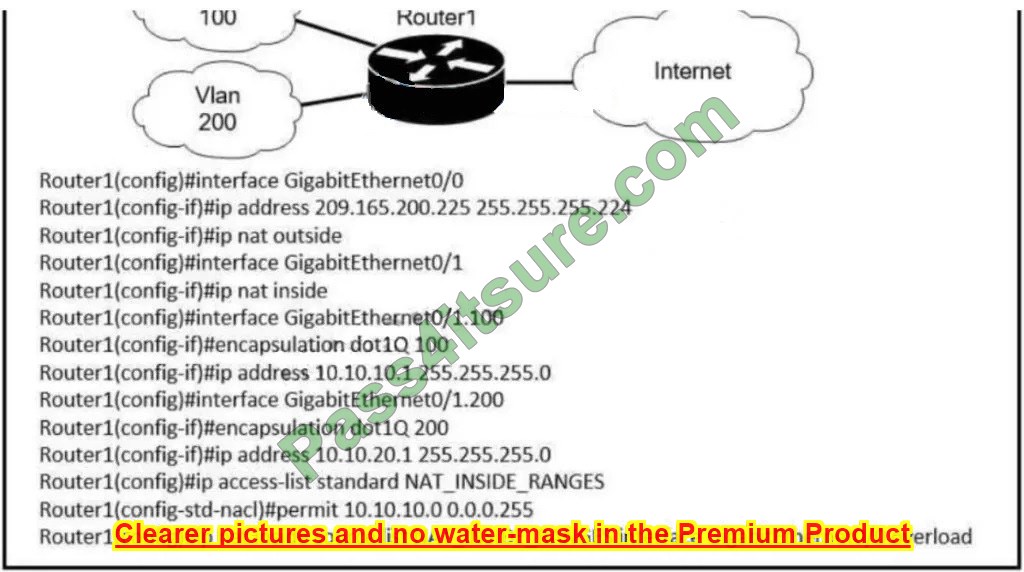
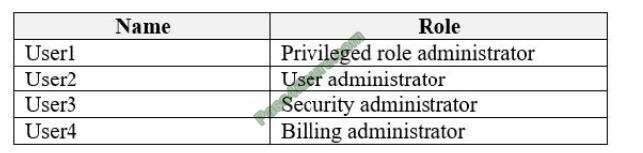
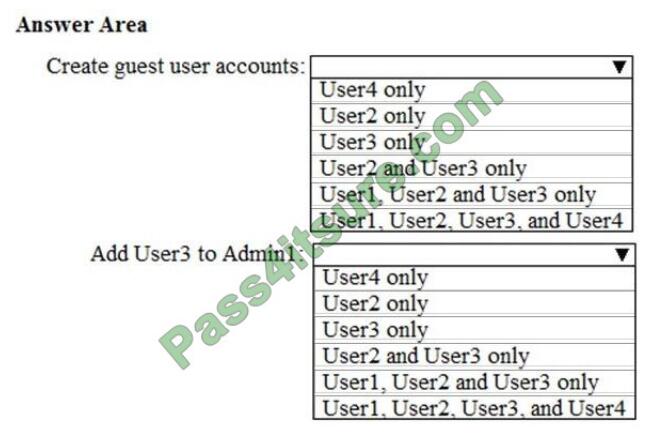
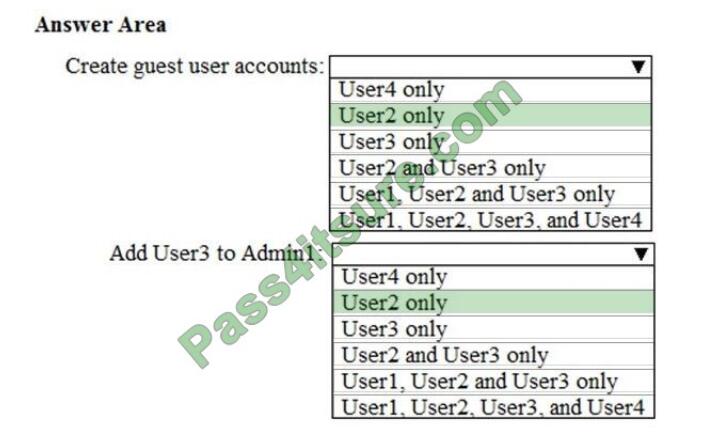
Question 8:
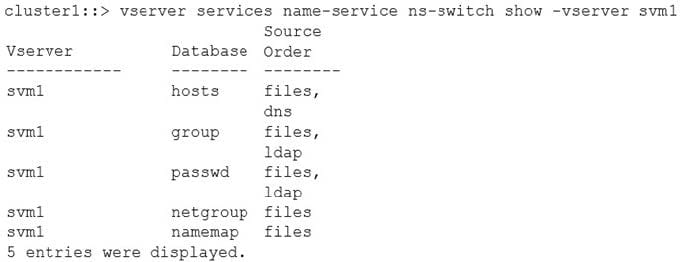
Referring to the exhibit, the UNIX user “prof1” will be looked up in which source first?
A. nis
B. dns
C. ldap
D. files
Correct Answer: B
Question 9:
You are using FCP and iSCSI protocols from your clients with ONTAP as the target. You want to ensure that storage failover (SFO) works correctly for your clients.
In this scenario, which two features of the initiator and the target will accomplish this task? (Choose two.)
A. LACP
B. MPIO
C. ALUA
D. SCSI
Correct Answer: BC
Reference: https://www.netapp.com/media/10680-tr4080.pdf
Question 10:
What are two supported cabling methods for a NetApp HCI compute node? (Choose two.)
A. 1-cable configuration
B. 2-cable configuration
C. 6-cable configuration
D. 4-cable configuration
Correct Answer: BC
Reference: https://library.netapp.com/ecm/ecm_download_file/ECMLP2856899 (11)
Question 11:
How many drive bays does a DS4246 shelf have?
A. 42
B. 12
C. 46
D. 24
Correct Answer: D
Question 12:
A customer asks what is the correct way to configure an ONTAP system for multi-tenancy. The customer wants to serve data and also protect data using SnapMirror from tenant A using network A and from tenant B using network B.
In this scenario, which statement is correct?
A. The customer must use different VLANs for the two tenants.
B. This setup can only work if tenant A and tenant B use a shared network infrastructure.
C. The customer must set up two different spaces for the two tenants.
D. Each node can only communicate with tenant A or tenant B, but not with both at the same time.
Correct Answer: B
Question 13:
A user can read and write some files on an NFS volume, but the user is unable to read all of the files in the volume.
In this scenario, which command will help you troubleshoot this problem?
A. security login create
B. security audit show
C. server security trace filter create
D. server export-policy check-access
Correct Answer: C
Question 14:
You are using AFF storage with the NVMe storage protocol on your Linux clients.
In this scenario, which NVMe feature must be present and enabled for the client to see storage failover happen?
A. Asymmetric Namespace Access (ANA)
B. Multi-Path I/O (MPIO)
C. Asymmetric Logical Unit Access (ALUA)
D. NVMe Qualified Name (NQN)
Correct Answer: B
Question 15:
For testing purposes, your customer decides to use FC on a single-node ONTAP cluster. There is only one host that the customer expects to use. High availability is not a concern for this test. The customer connects the host directly to the ONTAP node. The LUN is set up, and the group is configured. When the customer tries to attach to the LUN from the host, the LUN is not seen by the host.
Which statement is correct in this scenario?
A. Multipathing must be used and connected to another FC path.
B. NPV must be enabled on the host before trying to attach to the LUN.
C. NPIV must be enabled on the host before trying to attach to the LUN.
D. An FC switch must be used with ONTAP.
Correct Answer: B
2024 New NS0-194 Dumps NS0-194 Practice Questions
From: Pass4itSure
Number of issues: 10/60
Updated: Apr 16, 2024
Q1:
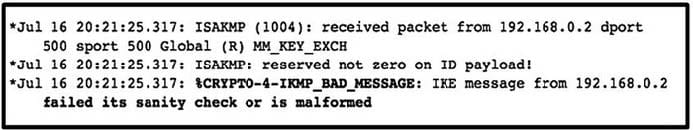
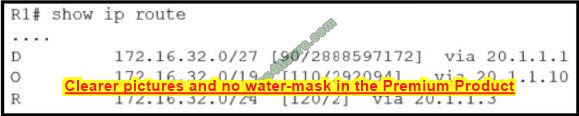
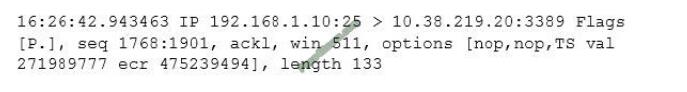
You have an ONTAP 2-node cluster. You run a read/write test workload against an SMB share, and it is slower than you expected. You run the same test again, but this time you monitor the storage using a QoS command.
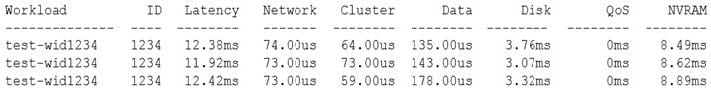
Referring to the exhibit, what is the problem?
A. There is a disk bottleneck.
B. An HA interconnect problem is present.
C. The SMB read sizes should be increased.
D. The NVRAM needs to be replaced.
Correct Answer: B
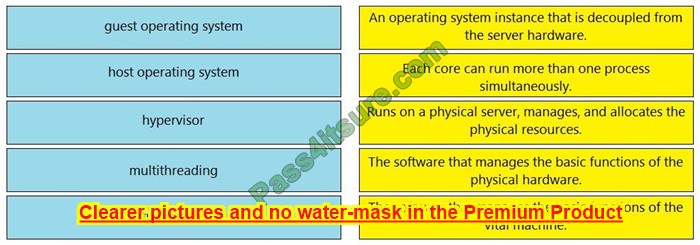
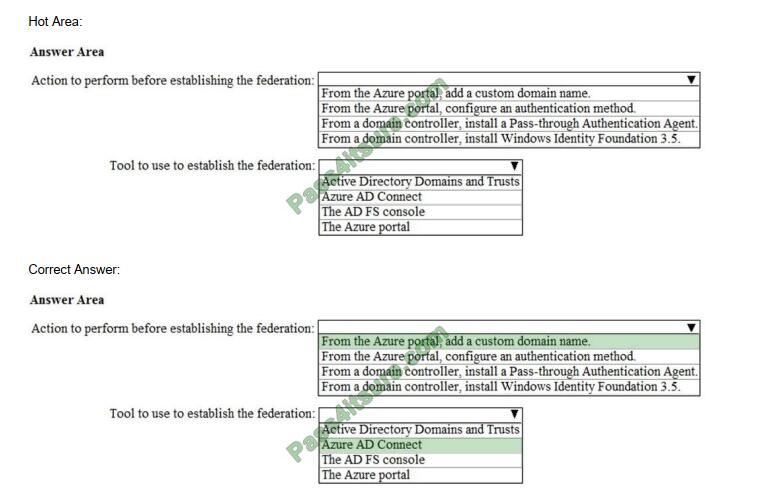
Q2:
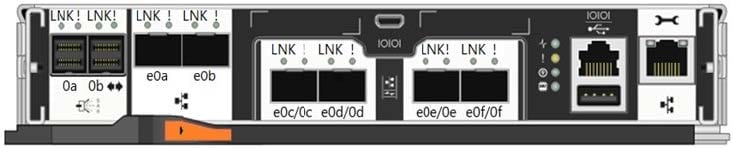
In the AFF A200 shown in the exhibit, which port is a CNA port?
A. |0|0|
B. e0c/0c
C. e0a
D. 0a
Correct Answer: B
Q3:
You want to use the supported method to upgrade the ONTAP version of a Cloud Volumes ONTAP instance from ONTAP 9.5 to ONTAP 9.6.
In this scenario, which NetApp tool accomplishes this task?
A. Cloud Manager
B. Cloud Insights
C. Active IQ Unified Manager
D. ONTAP System Manager
Correct Answer: D
Reference: https://docs.netapp.com/us-en/occm/task_updating_ontap_cloud.html#suspending-snapmirrortransfers
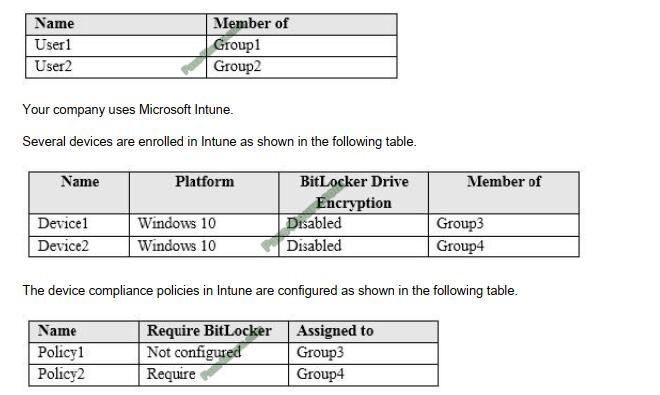
Q4:
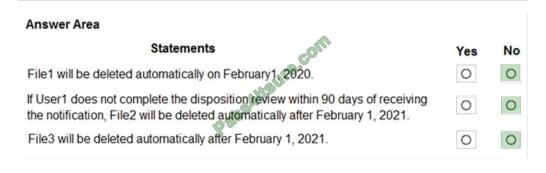
A volume was accidentally deleted two hours ago by another administrator. No backups exist.
In this scenario, what do you do to restore the data?
A. Use the ONTAP System Manager to recover the volume.
B. Use a volume snapshot to return the data to the active file system.
C. Use the volume recovery queue to restore the volume.
D. Use an aggregate snapshot to revert the aggregate to an earlier state.
Correct Answer: C
Q5:
Which two statements describe ONTAP NVRAM? (Choose two.)
A. ONTAP NVRAM is used as a read cache.
B. ONTAP NVRAM stores uncommitted writes.
C. ONTAP NVRAM is used as a write cache.
D. ONTAP NVRAM is battery-backed.
Correct Answer: BC
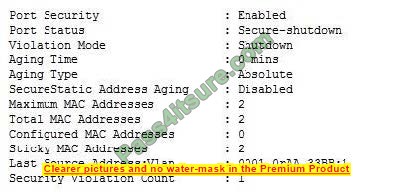
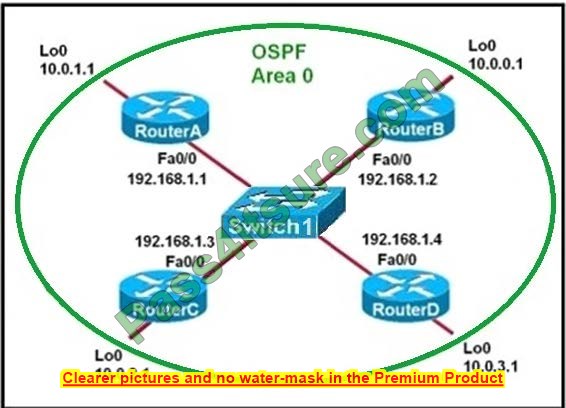
Q6:
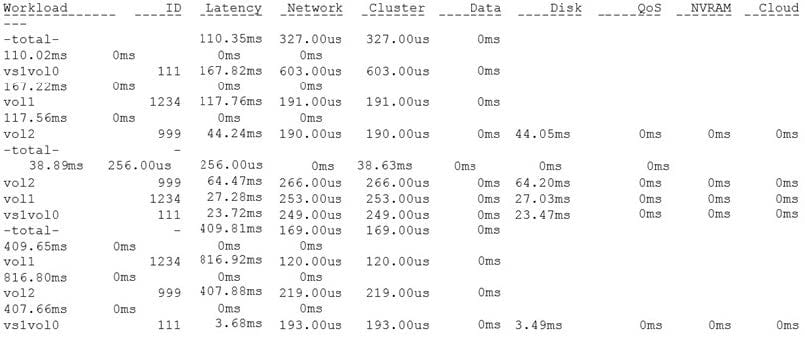
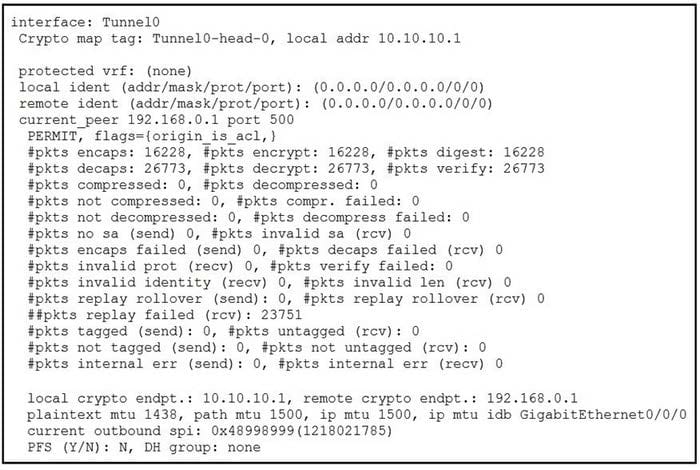
Referring to the exhibit, which two components should be examined? (Choose two.)
A. cluster switches
B. SAS adapter
C. network interface card
D. disk
Correct Answer: BD
Q7:
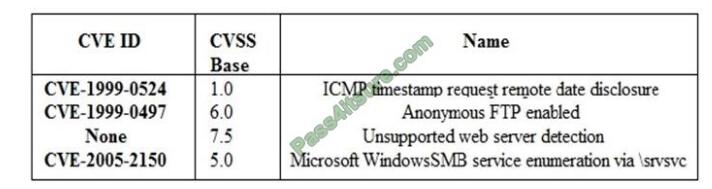
The details from within Active IQ Cluster Viewer are downloadable in which three file formats? (Choose three.)
A. PDF
B. CSV
C. XLS
D. DOC
E. HTML
Correct Answer: ABC
Q8:
Which NetApp technology enables a volume to span across one or more aggregates and one or more NetApp nodes?
A. FlexVol
B. Flash Pool
C. Flash Cache
D. FlexGroup
Correct Answer: D
Reference: https://www.netapp.com/pdf.html?item=/media/17251-tr4571apdf.pdf (3)
Q9:
Which NetApp technology enables you to perform block-based replication from NetApp Element software to Cloud Volumes ONTAP?
A. SyncMirror
B. SnapMirror
C. Cloud Sync
D. MetroCluster
Correct Answer: B
Q10:
Your Windows clients were able to access your CIFS SVM yesterday. Today they are no longer able to access the CIFS SVM on your NetApp cluster. Your IT security team just pushed out a new group policy to enhance security.
In this scenario, which statement is true?
A. Your CIFS SVM is not using DNS.
B. Your CIFS SVM is configured to use SMBv1 and SMBv2.
C. Your CIFS SVM is configured for NFSv3 access.
D. Your CIFS SVM is configured for the wrong domain.
Correct Answer: A
As you can see from the practice questions above, Pass4itSure NS0-194 dumps are always updated to provide you with the latest exam questions.
The importance of exam preparation
Proper exam preparation is crucial for achieving your certification goals. Without thorough preparation, you may find it difficult to pass the NS0-194 exam and obtain the desired certification. The exam covers a wide range of topics, including troubleshooting, installation, and configuration of NetApp storage systems. By dedicating adequate time and effort to exam preparation, you can enhance your understanding of these concepts and increase your chances of success.
Overview Of New NS0-194 Dumps
The new NS0-194 dumps provide a comprehensive and structured approach to exam preparation. These dumps are created by industry experts who have extensive knowledge and experience in the field. They have carefully curated the content to align with the exam objectives, ensuring that you cover all the essential topics. The dumps include practice questions, sample scenarios, and detailed explanations to help you grasp the concepts effectively.
Benefits Of Using New NS0-194 Dumps For Exam Preparation
There are several benefits to using the new NS0-194 dumps for your exam preparation.
- Firstly, they offer a convenient and flexible study option. You can access the dumps anytime, anywhere, allowing you to study at your own pace.
- Additionally, the dumps provide a realistic exam experience by simulating the actual exam environment. This helps you become familiar with the format and structure of the NS0-194 exam, reducing exam anxiety and improving your performance.
Features Of The New NS0-194 Dumps
The new NS0-194 dumps come with a range of features that facilitate effective learning. One of the key features is the comprehensive coverage of exam topics.
Another notable feature of the new NS0-194 dumps is the inclusion of practice questions and mock exams. By practicing with these questions, you can familiarize yourself with the types of questions you are likely to encounter, improving your ability to answer them accurately and efficiently.
How to Use the New NS0-194 Dumps Effectively
To make the most of the new NS0-194 dumps, it is essential to have a structured study plan.
Start by familiarizing yourself with the exam objectives and syllabus. This will help you identify the areas where you need to focus your efforts. Divide your study time into manageable chunks and allocate sufficient time to each topic.
While going through the dumps, make sure to read the explanations carefully and understand the underlying concepts. Rather than simply memorizing the answers, strive to comprehend the reasoning behind each solution. This will not only help you during the exam but also in real-world scenarios.
Additionally, take advantage of the practice questions and mock exams provided in the dumps. These are invaluable tools for self-assessment and can help you gauge your level of preparedness. Identify any weak areas and revisit the corresponding topics to strengthen your understanding.
Other Resources For Exam Preparation
While the new NS0-194 dumps are an excellent resource for exam preparation, it is always beneficial to explore additional study materials.
- Official NetApp documentation
- Online forums
- Community groups to gain a broader perspective on the exam topics.
- Engaging in discussions with fellow candidates can provide valuable insights and help clarify any doubts you may have.
Tips for Maximizing Your Exam Performance
In addition to using the new NS0-194 dumps, several tips can help maximize your exam performance:
- Create a study schedule and stick to it. Consistency is key in exam preparation.
- Take regular breaks during study sessions to avoid burnout and maintain focus.
- Practice time management during the exam to ensure you complete all the questions within the allocated time.
- Familiarize yourself with the exam format and structure beforehand to reduce exam anxiety.
- Utilize mnemonic devices or other memory aids to remember key concepts and information.
By implementing these tips and utilizing the new NS0-194 dumps, you can significantly enhance your chances of success in the certification exam.
Conclusion and Final Thoughts
Obtaining the NS0-194 certification can open up numerous career opportunities in the IT industry. To maximize your exam performance and achieve your certification goals, it is essential to invest time and effort into exam preparation. The new NS0-194 dumps provide a valuable resource to help you prepare effectively.
With the new NS0-194 Dumps 2024 https://www.pass4itsure.com/ns0-194.html new practice questions in PDF or VCE format, you can take the exam with confidence and increase your chances of success. Start your certification journey today and open up new possibilities for your career.