CISSP Dumps Updated | Master the CISSP exam with confidence

If you’re preparing for the CISSP exam, we’ll take care of it. Our updated CISSP dumps help you master the CISSP exam with confidence.
The latest Pass4itSure CISSP dumps https://www.pass4itsure.com/cissp.html With 1703 practice questions and answers, you’ll gain hands-on experience with the types of questions and scenarios encountered in the actual exam. This is important to ensure that you pass the exam confidently.
Best quality CISSP dumps:
If you are looking for high-quality and real CISSP dumps, you should try our Pass4itSure CISSP dumps. We at Pass4itSure provide the highest quality and up-to-date exam materials that really help candidates master the exam with confidence.
Difficulties encountered in the ISC certification CISSP exam:
- Not being able to dedicate yourself to studying for the CISSP exam all day is always busy.
- There is no planning to prepare for the CISSP exam. Start here, start there.
- The correct CISSP dumps data is not recognized, and there are too many fake outdated dumps on the market.
Don’t worry, with Pass4itSure CISSP dumps, none of this is a problem. Pass4itSure will not only help overcome difficulties in the exam but will also teach you to master the CISSP exam with confidence.
Genuine And Updated CISSP Exam Questions
Question 1:
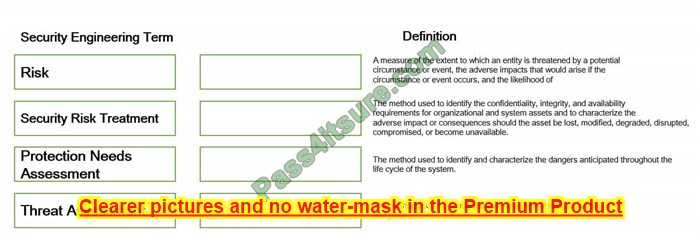
DRAG DROP Drag the following Security Engineering terms on the left to the BEST definition on the right.
Select and Place:
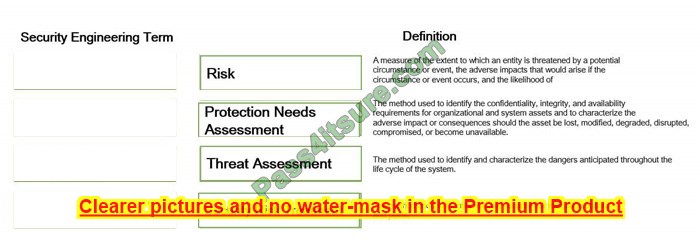
Correct Answer:
Question 2:
HOTSPOT
In the network design below, where is the MOST secure Local Area Network (LAN) segment to deploy a Wireless Access Point (WAP) that provides contractors access to the Internet and authorized enterprise services?
Hot Area:

Correct Answer:

Question 3:
HOTSPOT
Identify the component that MOST likely lacks digital accountability related to information access. Click on the correct device in the image below.
Hot Area:
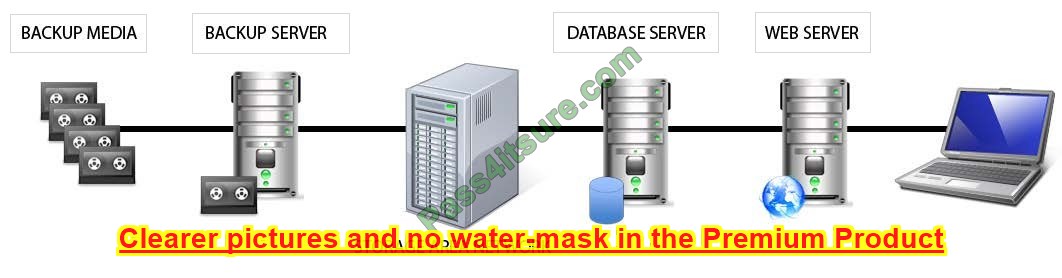
Correct Answer:
Question 4:
DRAG DROP
Place in order, from BEST (1) to WORST (4), the following methods to reduce the risk of data remanence on magnetic media.
Select and Place:
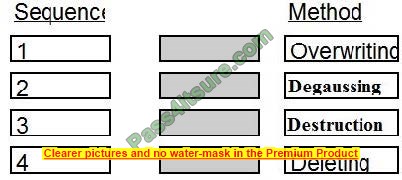
Correct Answer:

Question 5:
DRAG DROP
Match the access control type to the example of the control type. Drag each access control type net to its corresponding example.
Select and Place:

Correct Answer:

Question 6:
DRAG DROP
Given the various means to protect physical and logical assets, match the access management area to the technology.
Select and Place:

Correct Answer:
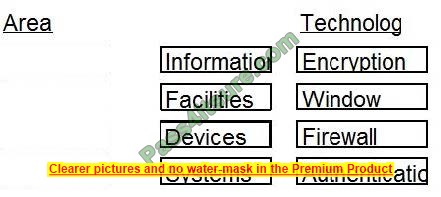
Question 7:
DRAG DROP
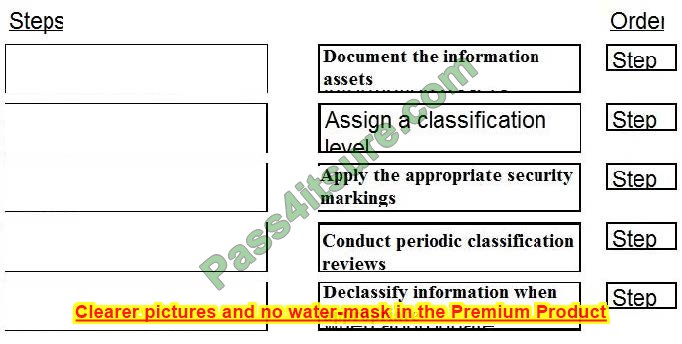
Place the following information classification steps in sequential order.
Select and Place:

Correct Answer:
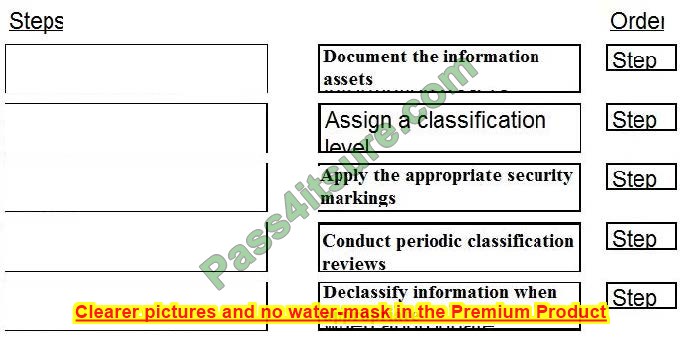
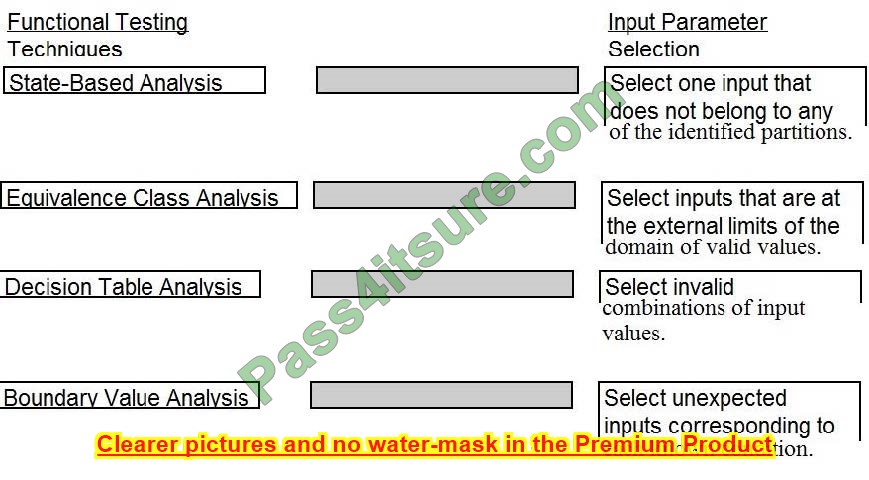
Question 8:
DRAG DROP
A software security engineer is developing a black box-based test plan that will measure the system\’s reaction to incorrect or illegal inputs or unexpected operational errors and situations. Match the functional testing techniques on the left with the correct input parameters on the right.
Select and Place:
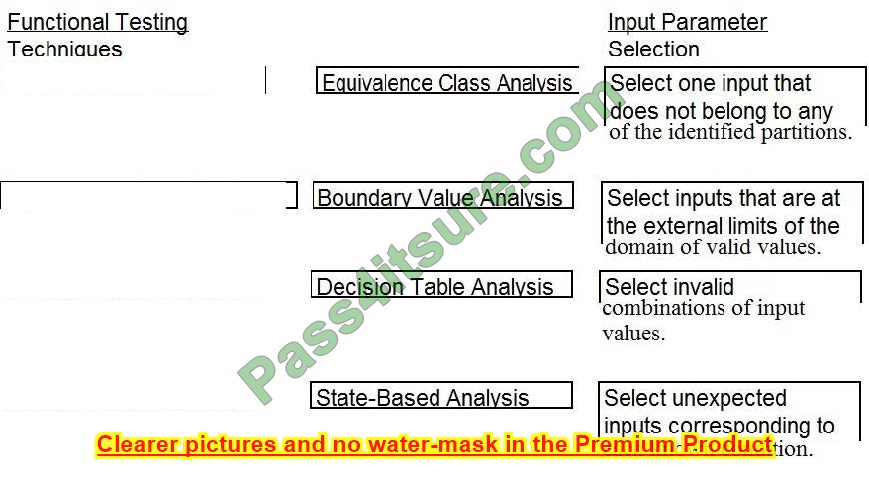
Correct Answer:
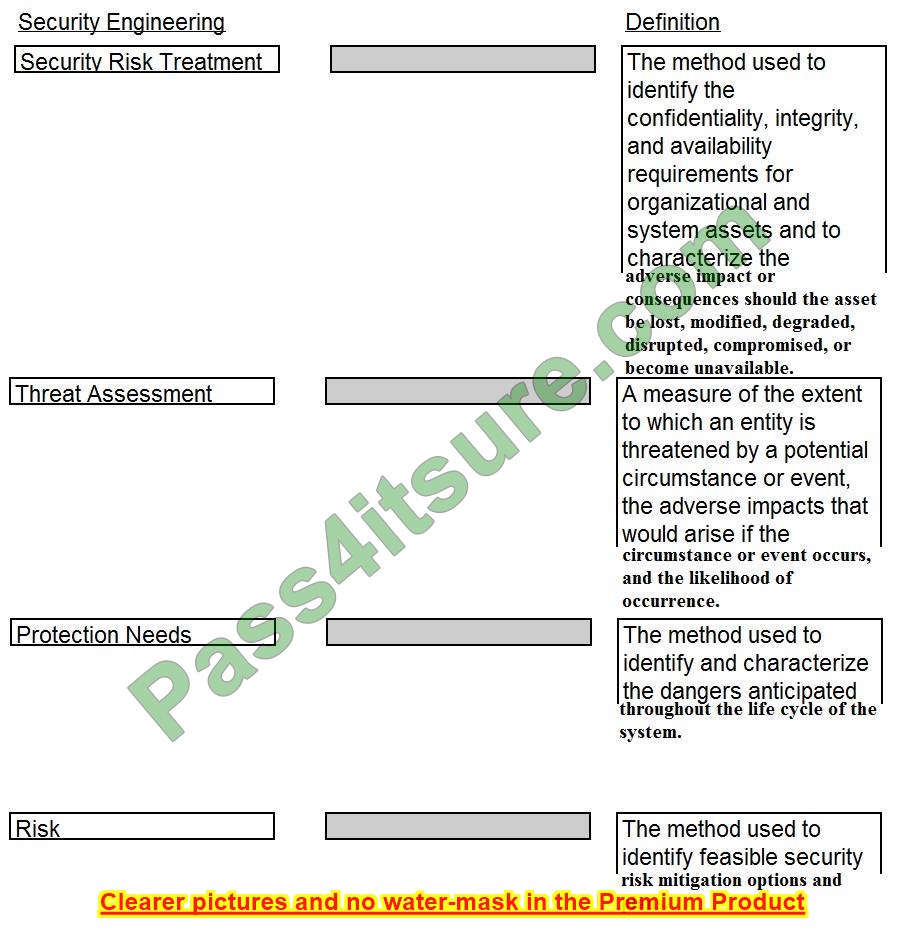
Question 9:
DRAG DROP
Drag the following Security Engineering terms on the left to the BEST definition on the right.
Select and Place:
Correct Answer:
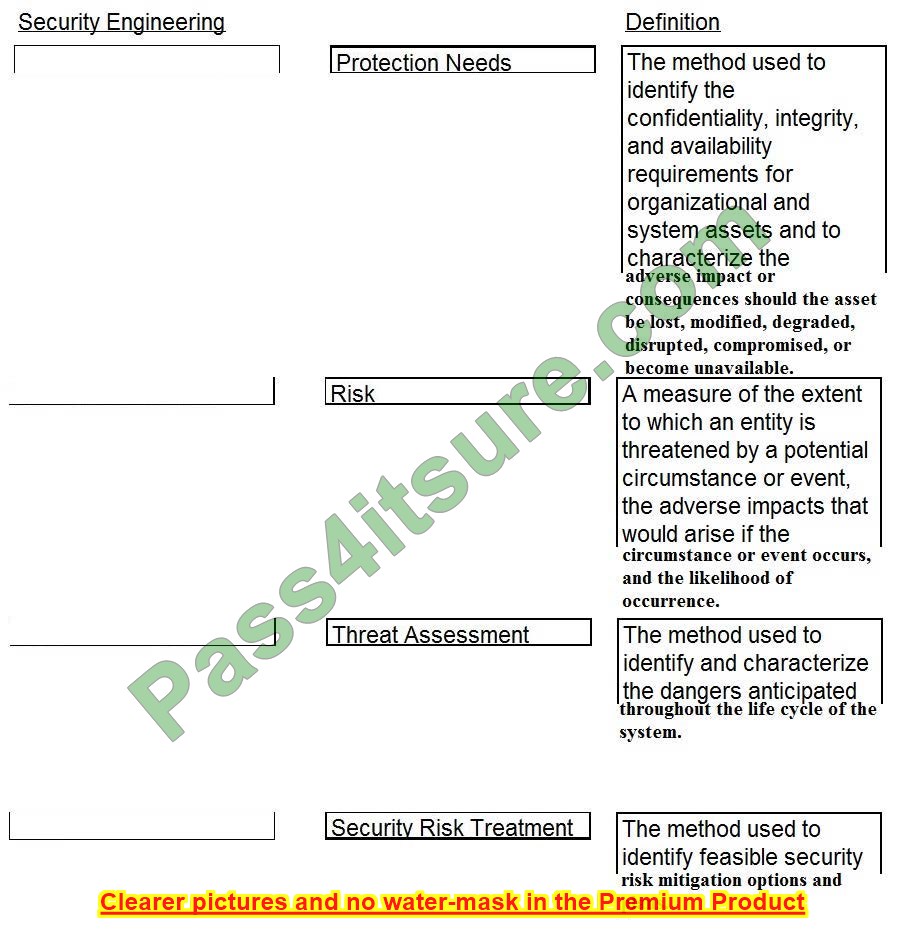
Question 10:
DRAG DROP
Match the types of e-authentication tokens to their description.
Drag each e-authentication token on the left to its corresponding description on the right.
Select and Place:

Correct Answer:
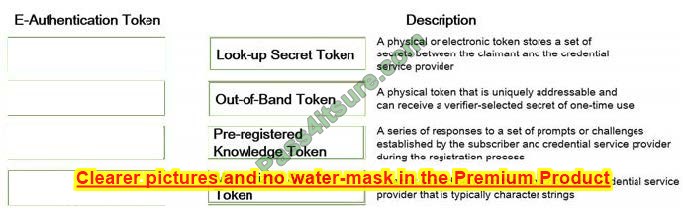
Question 11:
DRAG DROP
During the risk assessment phase of the project, the CISO discovered that a college within the University is collecting Protected Health Information (PHI) data via an application that was developed in-house. The college collecting this data is
fully aware of the regulations of the Health Insurance Portability and Accountability Act (HIPAA) and is fully compliant. What is the best approach for the CISO?
Below are the common phases to creating a Business Continuity/Disaster Recovery (BC/DR) plan. Drag the remaining BC\DR phases to the appropriate corresponding location.
Select and Place:
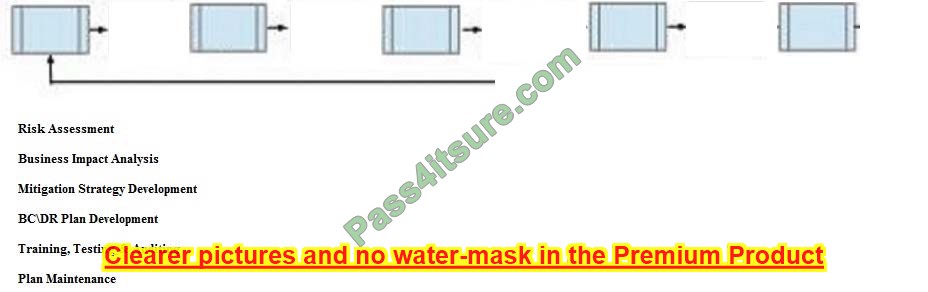
Correct Answer:

Question 12:
DRAG DROP
Match the name of the access control model with its associated restriction.
Drag each access control model to its appropriate restriction access on the right.
Select and Place:

Correct Answer:

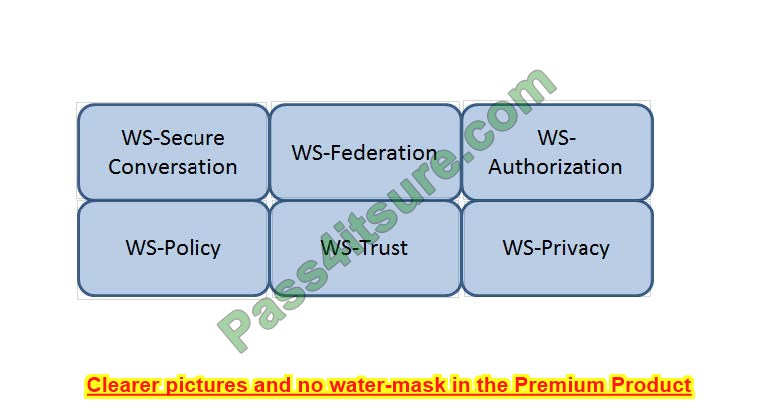
Question 13:
HOTSPOT
Which Web Services Security (WS-Security) specification negotiates how security tokens will be issued, renewed, and validated? Click on the correct specification in the image below.
Hot Area:
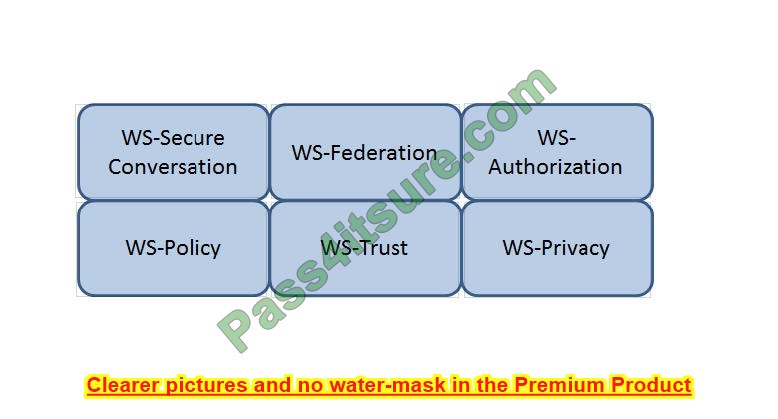
Correct Answer:
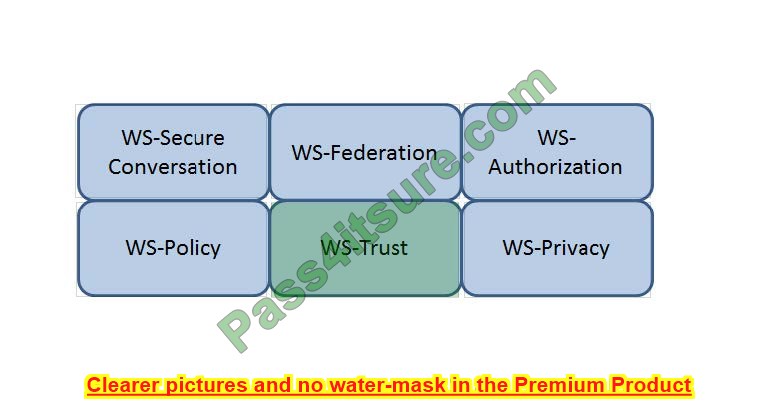
Question 14:
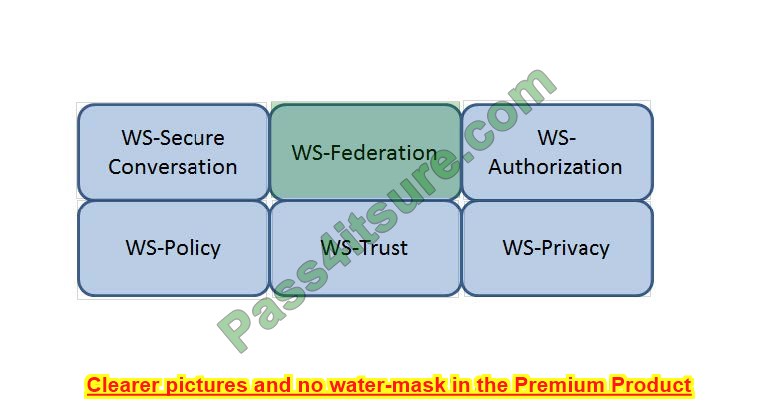
HOTSPOT
Which Web Services Security (WS-Security) specification maintains a single authenticated identity across multiple dissimilar environments? Click on the correct specification in the image below.
Hot Area:
Correct Answer:
Question 15:
DRAG DROP
Match the objectives to the assessment questions in the governance domain of the Software Assurance Maturity Model (SAMM).
Select and Place:

Correct Answer:

The latest CISSP pdf is free to download: https://drive.google.com/file/d/1Lc9azzeV1HTKikIleVKfkkAm_6V4WjOR/view?usp=share_link
So:
Everyone wants to confidently master the CISSP exam, you, me, he is. So use Pass4itSure CISSP dumps to make your dreams come true, the latest and most complete CISSP dumps https://www.pass4itsure.com/cissp.html you need to have.